Employees frequently collaborate with others and need to access shared corporate resources. Among the different protocols that facilitate network communication, the server message block (SMB) protocol is a popular resource for smooth collaboration across a network.
The SMB protocol enables network communication and empowers users to access files, printers, and other resources on a network. In this guide, we will learn about SMB and cover its working principle, integrations, best practices, and more.
What is SMB?
The server message block protocol is a network communication protocol for providing shared access to files, printers, serial ports, and other resources between nodes on a network.
Also known as the common internet file system (CIFS), it’s a client-server communication protocol in which a client sends a request for services, and the server responds accordingly. It’s the most popular protocol used in the workplace for file sharing.
SMB is a network communication protocol developed by IBM in the 1980s and later adopted by Microsoft. Since then, it has been the primary protocol in Windows networking. However, macOS and Linux also have client components that connect with SMB resources.
SMB in the business context
Small and midsized businesses rely on the SMB protocol for file sharing and collaboration. It enables SMB businesses to share resources and improve productivity. They also use it to navigate hosting solutions and manage their IT infrastructure.
Some of the ways SMB helps small and medium businesses include:
-
File sharing: It allows users to share and access files stored on servers or network-attached storage (NAS) devices.
-
Printer sharing: SMB can connect multiple printers to the network and let all users access them from their systems.
-
Remote access: Employees working remotely can use SMB to access corporate files.
-
Backup and data recovery: It’s used in backup solutions to assist in storing and retrieving backup data.
-
Distributed file systems: For a small and midsized business with distributed file systems, SMB can provide a centralized data storage approach.
In short, SMB refers to centralized network resources management and accessibility. It also allows small and medium-sized businesses to add more devices/users as they grow.
The easiest help desk system for a team like yours
Discover HelpDesk
How the SMB protocol works
The SMB protocol enables applications and users to access files on remote servers and connect to other resources, including printers, mail slots, and named pipes.
SMB offers client applications a controlled and secure way of opening, reading, moving, creating, and updating files on remote servers.
The protocol runs at the application layer but depends on TCP and IP protocols for transport. Its server components use TCP port 445 and can also interact with programs designed to receive clients’ SMB requests.
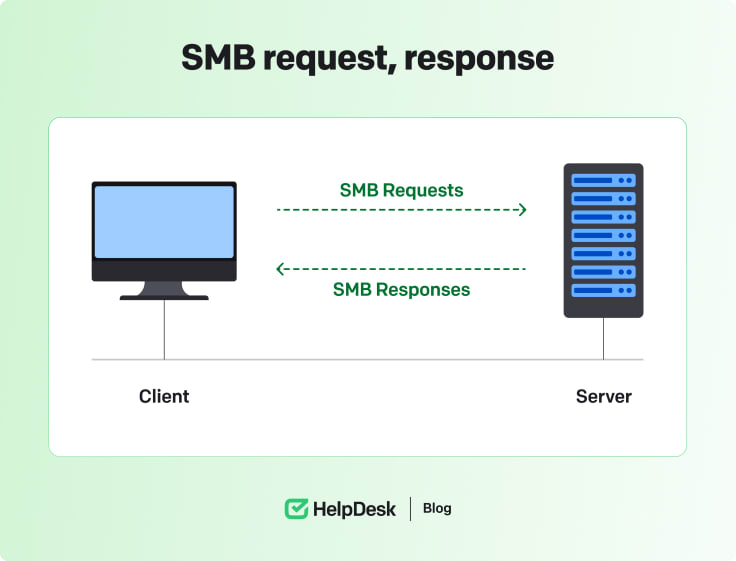
The below steps further clarify the working principle of SMB:
-
The client (user computer/smartphone/printer) sends an SMB request to the server to set up a connection.
-
The server receives the request and returns the SMB response to the client.
-
A communication channel is established after the response is received.
-
The device can now interact with the server to perform specific actions.
Consider that you want to use SMB to print a document. Let’s assume the office printer is linked to the administrator’s computer. To access the printer, your computer (the client) sends the administrator’s computer (the server) a request to print using the SMB protocol. Afterward, the server responds to the request with the status like printer, queued, or out of ink.
Opportunistic locking
Opportunistic locking (OpLocks) is a mechanism in the SMB protocol designed to improve performance by controlling the client’s caching of network files. It lets users save the cache files locally and reduces network traffic.
There are four types of opportunistic locks:
-
Level 1 OpLocks: This type empowers the client to read and write data from a file and cache it locally. It assumes that no other client has access to the file.
-
Level 2 OpLocks: This type is usable when multiple clients read the duplicate files but do not modify them. A Level 2 OpLock allows clients to cache read operations but still interact with the server for write operations.
-
Batch OpLocks: This type regulates file openings and closings. It opens the batch file on the computer (server) and keeps it open. It eradicates the need to send overhead multiple open and close requests across the network. It works best when a file is repeatedly opened and closed (like batch script execution)
-
Filter OpLocks: This type is similar to Level 2 but locks a file to avoid write or delete access. Clients can read duplicate files without dealing with the conflict between opening the file and acquiring a lock. Microsoft recommends using Level 2 Oplocks for general purposes and Filter OpLocks for specific sharing behavior.
SMB protocol versions
Since the SMB protocol’s inception, several updates/versions have been released to optimize functionality, security, and scalability.

SMB protocol safety and security
The SMB protocol has faced security concerns, particularly with the Petya and WannaCry ransomware attacks 2017. These ransomware attacks used an SMB 1.0 vulnerability to load malware on exposed clients and then spread it across networks.
Microsoft introduced the patch to fix the vulnerability. Despite that, experts recommend disabling SMB 1.0 on all devices.
The release of SMB 3.0 and later versions effectively tackled these security concerns. For example, the SMB 3.0 version introduced secure dialect negotiation and end-to-end data encryption to improve security. It helps protect against MitM attacks and eavesdropping.
SMB 3.1.1 has further enhanced security with updated encryption capabilities and pre-authentication integrity.
The easiest help desk system for a team like yours
Discover HelpDesk
CIFS vs. SMB
SMB and CIFS are often interchangeable. However, CIFS is the early dialect of the SMB that Microsoft developed. So, it refers to only a single SMB implementation. It matches SMB 1.0 in both the application interfaces and technical documentation.
1. Security
CIFS and SMB 1.0 have different security protection levels. SMB 3.0 and later versions provide more robust security protection than CIFS, limiting its use.
2. Network Performance
CIFS and SMB also differ in network performance. CIFS causes network inefficiencies and performance issues due to chattiness. It causes high latency and needs frequent acknowledgments.
SMB 2.0 and later versions have significantly improved the protocol’s efficiency. They have reduced the extensive commands and subcommands from hundreds to just 19. Furthermore, SMB 3.0 introduced SMB Multichannel, which decreased latency and improved network efficiency.
Implementations and integrations
Multiple solutions now make SMB implementation and integration possible. The most widely used SMB implementation is via Samba.
Samba is an open-source re-implementation of the SMB networking protocol for Unix-like systems. It provides file and print services for Microsoft Windows clients and can integrate with a Windows NT 4.0 server domain. It includes a server that allows client types to access SMB resources. Moreover, it’s compatible with different SMB dialects.
Other than Samba, other well-known third-party implementations include:
-
NSMB: It’s a family of in-kernel implementations of SMB clients in BSD operating systems.
-
NQ: It’s a portable SMB client and server implementation that involves a storage SMB Server, a Pure Java SMB Client, and an embedded SMB stack implementation.
-
MoSMB: A high-performing and scalable SMB3 server for Linux. It’s best suited for managing enterprise workloads and can integrate with different storage backends.
-
Fusion file share: A proprietary SMB server provides seamless sharing and storage solutions. It can be integrated with NAS devices to provide secure and fast SMB connectivity.
-
KSMBD: It’s an in-kernel SMB server implementation for Linux. It improves file I/O performance by handling the SMB protocol within the kernel space.
Third-party implementations
Third-party implementations of the SMB come with some unique benefits. They offer various features such as:
-
SMB direct: It offers remote direct memory access (RDMA) and the ability to support network adaptors.
-
SMB multichannel: It allows servers to use multiple network connections simultaneously.
-
Transparent failover: It allows clients to switch between servers without interrupting ongoing operations.
Third-party implementations provide alternatives to the standard SMB protocol and can offer improved performance and functionality.
Cloud file data migration
It’s worth noting that cloud file data migration can be challenging due to the large number of small files and high network traffic.
The SMB protocol requires many back-and-forth handshakes, which increases network traffic and latency. The WAN latency and limited bandwidth can prevent file data transfers from becoming slow, unreliable, and difficult to manage.
Best practices and considerations
Now that we have cleared the basics and principles of the SMB protocol let’s highlight a few best practices and considerations to maximize your use of SMB:
-
Small to midsized businesses should consider implementing SMB 3.0 or later versions for improved security and performance.
-
Regularly updating SMB protocol versions and configurations can help prevent security vulnerabilities.
-
To ensure efficient file sharing and collaboration, navigating hosting solutions and managing IT infrastructure are essential for SMBs.
-
Regulate outbound SMB destinations using a firewall with advanced controls to avoid connections with malicious servers.
-
Use strong access control measures to restrict only file and folder access to authorized users.
-
Make sure all user accounts accessing SMB are using strong passwords.
-
Train employees about SMB usage and security vulnerabilities to avoid incidents.
The SMB protocol usage demands a strong emphasis on security to avoid potential breaches.

For example, HelpDesk provides a powerful ticketing management platform. Similarly, you can use its AI email generator to generate personalized business emails. Besides that, consider exploring resources like the latest business email writing guides that help you write effective emails and understand the email structure to ensure clear and professional communication.
Summary
The SSMB protocol is a vital tool for network communication, especially for small and midsized businesses. We can significantly boost file-sharing and collaboration by deepening our understanding of SMB and its diverse applications.
Embracing best practices and keeping up with the latest SMB versions empowers businesses to achieve efficient and secure file management. Let’s explore these opportunities together and unlock the full potential of our network capabilities!


